Single sign-on (SSO)
Single sign-on lets your team sign in to Enigma Console using your organization's identity provider (IdP). Enigma supports any SAML 2.0 compliant provider, including Okta, Azure AD, Google Workspace, and OneLogin.
Prerequisites
Before you begin, verify that you have:
- Admin or Owner role in your Enigma organization
- Administrative access to your identity provider
- Ability to create SAML applications in your IdP
How SSO works
Enigma uses SAML 2.0 with a service provider (SP) initiated flow:
- A user visits
https://console.enigma.com/loginand clicks Log in with SSO - The user enters their email address
- Enigma redirects them to your identity provider
- The user authenticates with your IdP
- Your IdP sends a SAML assertion back to Enigma
- Enigma validates the assertion and signs the user in
Step 1: Create a SAML application in your IdP
Start by creating a new SAML application in your identity provider. The exact steps vary by provider, but you typically need to:
- Navigate to your IdP's application catalog
- Create a new SAML 2.0 application
- Configure the application with placeholder values (you'll update these after configuring Enigma)
Keep your IdP configuration open. You'll return to it after completing the Enigma configuration.
Step 2: Configure Enigma
- Sign in to Enigma Console with your username and password
- Go to Team Members
- Click Configure Identity Provider
Provide your IdP's SAML metadata
You can provide your IdP's SAML metadata using either method:
| Method | Description |
|---|---|
| Metadata URL | Paste your IdP's metadata endpoint URL. Enigma fetches the metadata automatically and keeps it synchronized. |
| Metadata file | Upload the XML metadata document from your IdP. The file must use UTF-8 encoding. |
Choose one method. If you enter a URL, the file upload is disabled, and vice versa.
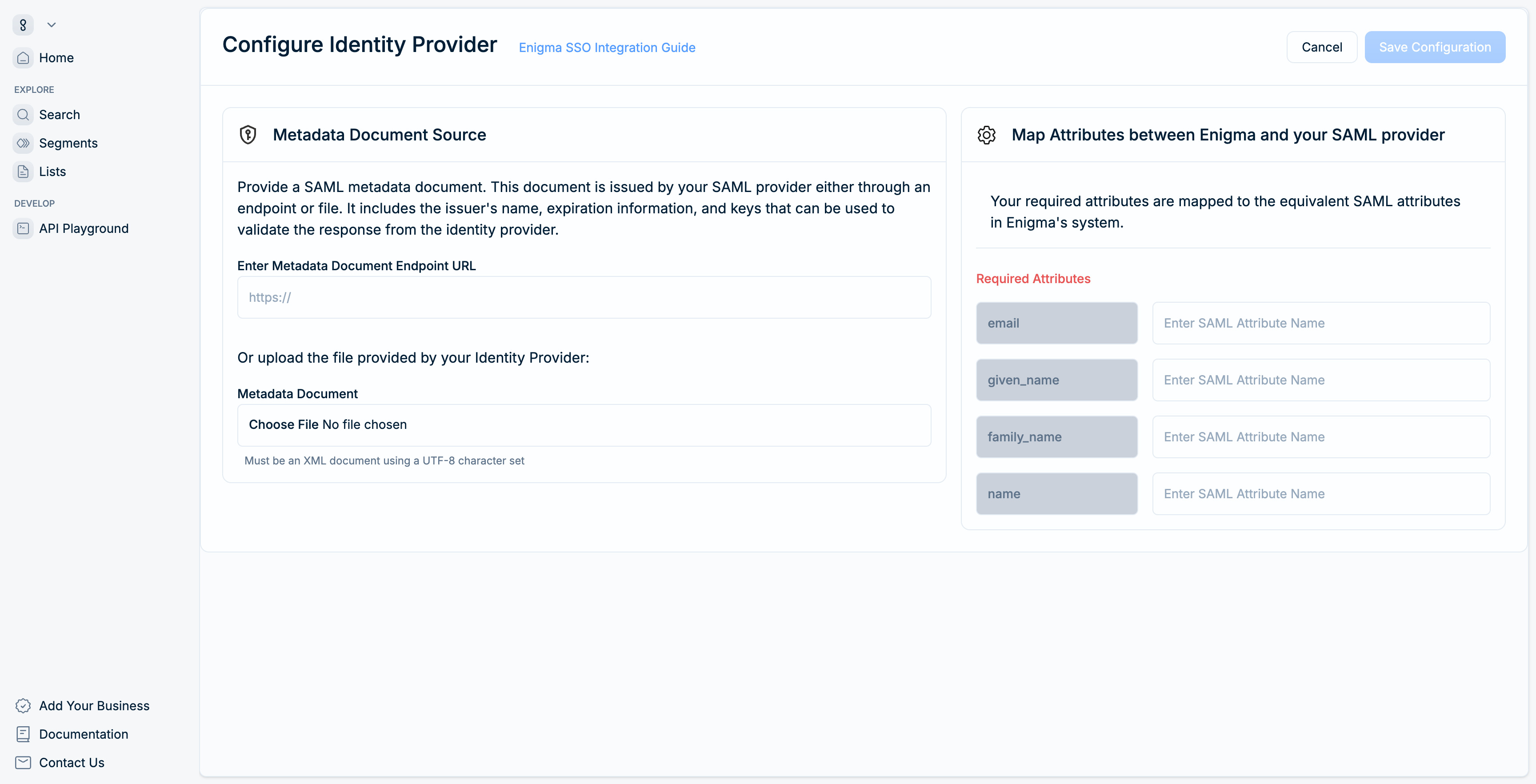
Map SAML attributes
Configure how your IdP's attributes map to Enigma user properties. Enter the exact attribute names your IdP sends in the SAML assertion.
| Enigma attribute | Description | Required | Common IdP attribute names |
|---|---|---|---|
email | User's email address | Yes | user.email, email, emailAddress |
given_name | User's first name | Yes | user.firstName, givenName, firstName |
family_name | User's last name | Yes | user.lastName, surname, familyName |
name | User's full display name | Yes | user.displayName, name, displayName |
The attribute names must match exactly what your IdP sends. For example, if your IdP sends Email but you configure email, authentication fails.
Click Save Configuration to save your settings.
Copy Enigma's sign-on settings
After you save your configuration, Enigma displays its service provider settings. Copy these values for the next step:
| Setting | Description |
|---|---|
| Assertion Consumer URL | The endpoint where your IdP sends SAML responses |
| Service Provider Entity ID | Enigma's unique identifier as a service provider |
Step 3: Update your IdP configuration
Return to your identity provider and update the SAML application:
- Set the Assertion Consumer Service (ACS) URL to the value you copied from Enigma
- Set the SP Entity ID (or Audience URI) to Enigma's Service Provider Entity ID
- Configure attribute mappings to send the required attributes (
email,given_name,family_name,name) - Assign users or groups to the application
Step 4: Test the connection
- Open a private or incognito browser window
- Go to
https://console.enigma.com/login - Click Log in with SSO
- Enter your email address
- Verify that you're redirected to your IdP and can authenticate
Configuration changes may take a few minutes to propagate. If the SSO flow doesn't work immediately, wait 2-3 minutes and try again.
Users must always start from the Enigma sign-in page. Clicking the Enigma application tile directly from your IdP dashboard (such as an Okta chiclet) doesn't work. Direct your users to https://console.enigma.com/login and have them click Log in with SSO.
Troubleshooting
Invalid SAML response error
This error typically indicates an attribute mapping problem:
- Verify that attribute names match exactly, including capitalization
- Check that your IdP is sending all four required attributes
- Confirm that your IdP's metadata URL is accessible from the internet
Users don't see the SSO option
- SSO sign-in is available at
https://console.enigma.com/login. Users must click Log in with SSO and enter their email - Configuration changes may take a few minutes to propagate. Wait 2-3 minutes and try again
Duplicate provider error
This error appears if your IdP has already been configured for another Enigma organization. Each IdP can only be linked to one Enigma organization. Contact Enigma support if you need to transfer an IdP configuration.